Are cybersecurity programs shaped more by perception than reality? Let's apply a little quantum theory to find out. In 1935, Erwin Schrödinger, an Austrian physicist and a founding father of quantum theory, offered a thought experiment about quantum physics to explain how scientific theory works. Schrödinger stated that if you placed a cat and something that could harm the cat in a box and sealed it, you would not know whether the cat was dead or alive until you opened the box. So until the box is opened, the cat is (in a sense) both. Setting all cats safely aside, the premise is that a scientific theory is right or wrong until it is tested and proven.
Cybersecurity programs are, in a sense, a scientific theory; no one can know for sure if one will work until it comes under attack. Until then, the program both works and fails. Many organizations go about thinking their cybersecurity programs are a success in the absence of proof. But we can also use Schrödinger's logic to view our cybersecurity programs as both compromised and secure. Looking at the box from the outside, we can have an assumption of breach or an assumption of a secure state. One never knows until they open the box.
Would stuffing the box with cyber defenses affect the cat's state? How would you know? Until the box is opened, one never knows the true security posture or the state of what is inside. But if we applied continuous security posture management to the box, we could improve the chances of the cat's survival.
You may be thinking, "Surely he must be getting to the point of this blog sometime soon." Here it is: Even if we cannot know the state of our cybersecurity programs, we can improve our odds of survival through continuous offensive security testing and validation to effectively test what is in the box.
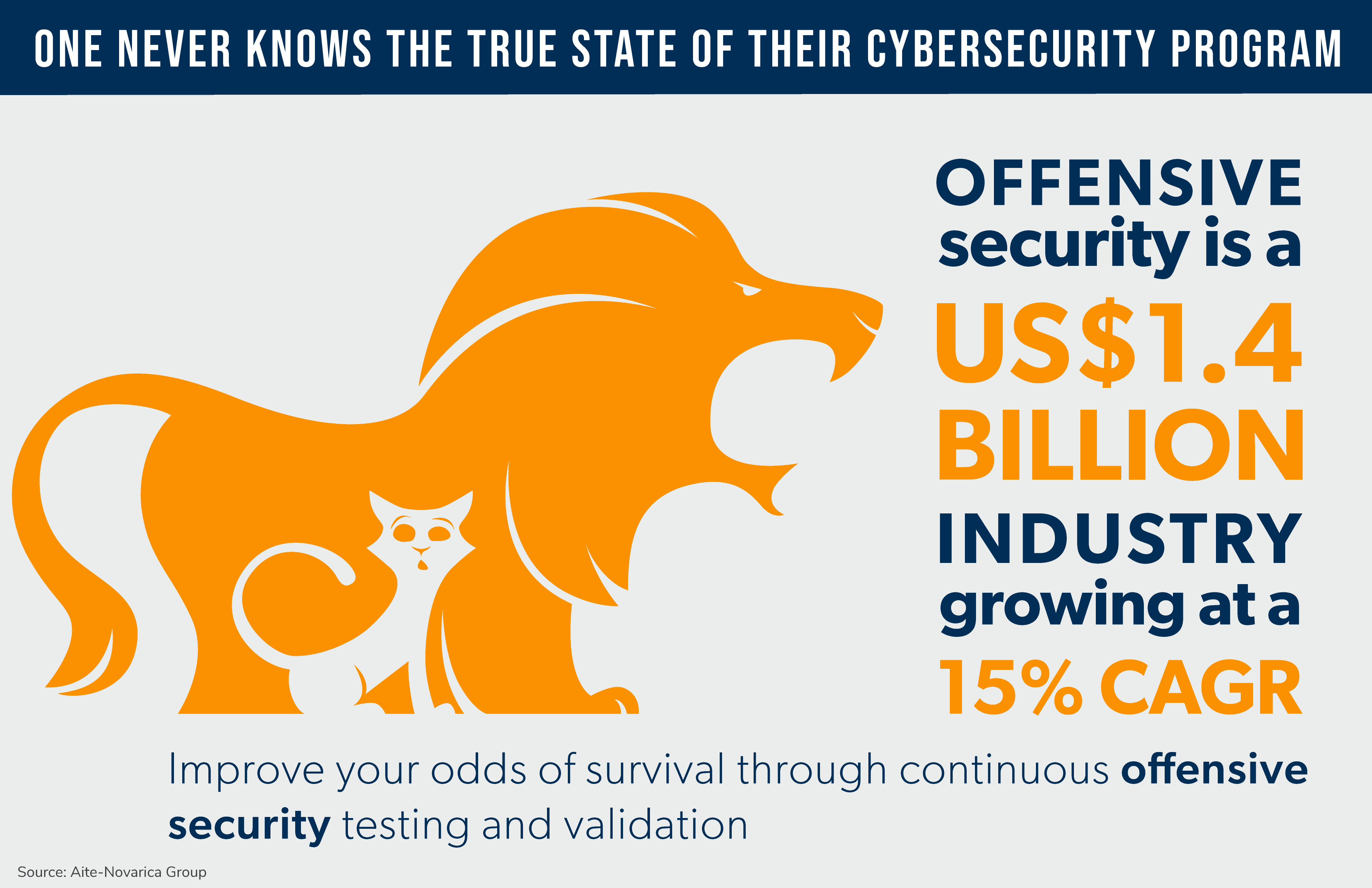
If you haven't sensed it yet, I think offensive security is the cat's meow. Offensive security is a US$1.4 billion industry, growing at a 15% CAGR. If you want to learn more, check out companies such as Bishop Fox, Cymulate, Pentera, and IBM's X-Force, which have established themselves as leaders in offensive security and adept at keeping precious cats safe from harm.
I will be adding more reports covering offensive security solutions later this year. In the meantime, here are a couple you may have missed: Attack Surface Management: Avoiding Device Whack-a-Mole and Threat Hunting: An Active Cyber Defense Strategy for a Hostile Cyber World. Have questions or comments? Contact me here.
Add new comment