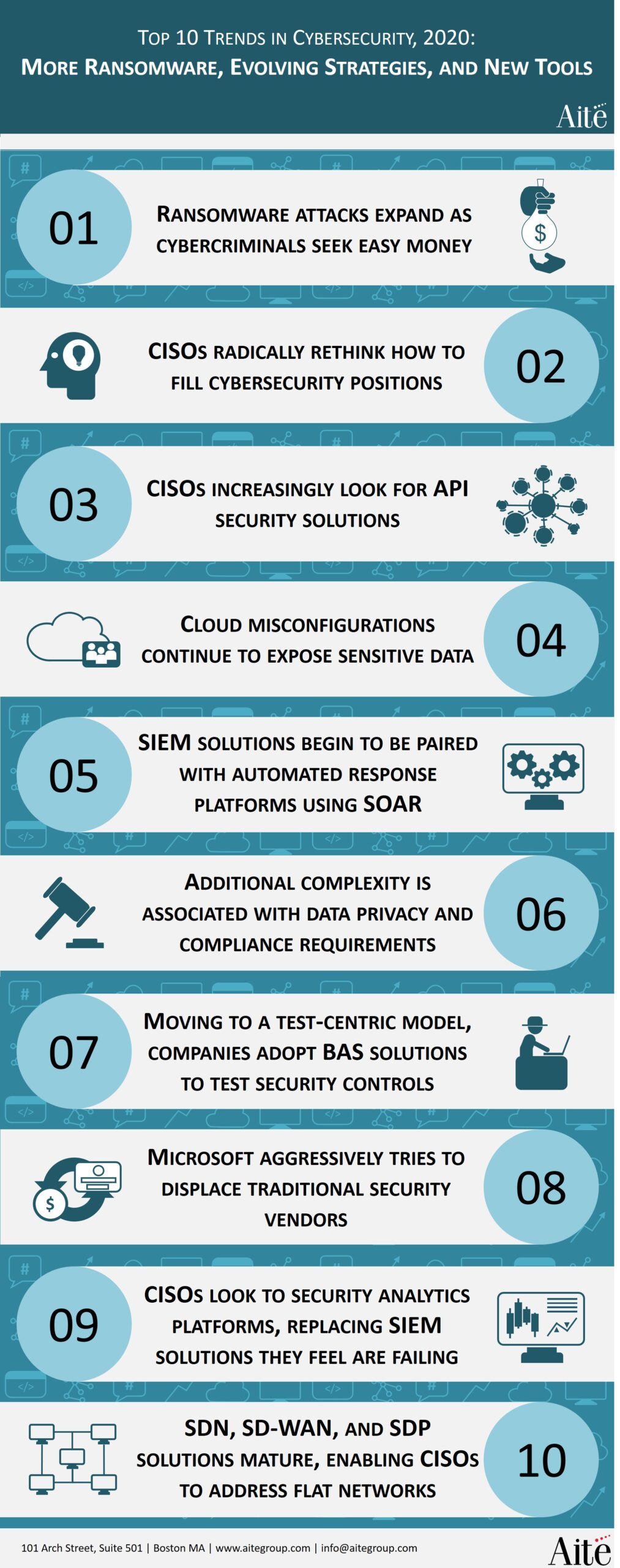
Boston, January 9, 2020 – The top cybersecuritytrends in 2020 will drive organizations’ cybersecurity strategies and investments, and capture the focus of their security leaders. Ransomware activities will target organizations of all sizes, which must look for specific solutions to bolster system and data availability as well as to optimize recovery processes. In addition, 2020 will be an inflection point for many legacy security controls, and companies will be required to move from nearly obsolete signature-based systems and to machine learning-powered solutions. Meanwhile, the lack of skilled cybersecurity professionals will worsen, and chief information security officers will have to look for new sources of talent and radically rethink how they staff their open roles.
This is an 18-page Impact Report. Clients of Aite Group’s Cybersecurity service can download this report.
This report mentions 42Crunch, Acronis, Amazon, Aqua, Arcadia Data, Arcserve, AttackIQ, BigID, BlackBerry Cylance, Check Point, CloudCheckr, Cloudflare, Commvault, Cronus, CrowdStrike, Cyberbit, Cybereason, Cybersponse, CyCognito, Cymulate, Dell EMC, Devo, DFLabs, Druva, FireEye, Forum Systems, Google, Guardicore, IBM, Illumio, Illusive Networks, Malwarebytes, Microsoft, Morphisec, OneTrust, Palo Alto Networks, Picus Security, Pridatect, Pulse Secure, SafeBreach, Salt Security, SAS Cybersecurity, Securonix, SentinalOne, Siemplify, Splunk, Swimlane, ThreatConnect, TrustArc, Unisys, WhiteHaX, and XM Cyber.
About the Author
Datos Insights
We are the advisor of choice to the banking, insurance, securities, and retail technology industries–both the financial institutions and the technology providers who serve them. The Datos Insights mission is to help our clients make better technology decisions so they can protect and grow their customers’ assets.
Other Authors
Datos Insights
We are the advisor of choice to the banking, insurance, securities, and retail technology industries–both the financial institutions and the technology providers who serve them. The Datos Insights mission is to help our clients make better technology decisions so they can protect and grow their customers’ assets.