Boston, December 8, 2020 – Financial institutions, fintech firms, and merchants need to take a step back and review their authentication control framework if it has been a few years since that framework was last reviewed. But defining a control framework for authentication should not be taken lightly. A company’s reputation and financial health are at risk, not to mention the risks to consumers.
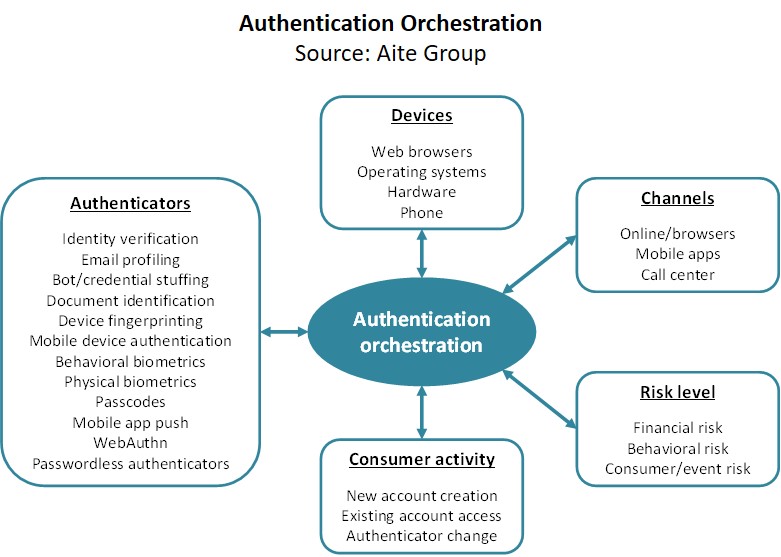
This report is for companies who interact with customers in non-face-to-face channels such as online, mobile, and call centers. It exposes the shortcomings and challenges of common but outdated identity proofing and customer authentication processes and solutions, and defines a framework for modernizing them. It draws upon information gathered from industry research, numerous briefings with global industry players, and standards organizations in various parts of the world. It is also based on guest author Ken Palla’s 15 years of experience managing online security threat analysis and implementing solutions.
This 37-page Impact Report contains four figures and 17 tables. Clients of Aite Group’s Fraud & AML service can download this report, the corresponding charts, and the Executive Impact Deck.
This report mentions Acceptto, Accertify, Acuant, Acxiom, Akamai, Amazon, Apility, Appdome, Apple, Aratek, Arkose Labs, ArkOwl, Au10tix, Auth0, AuthArmor, AuthenticID, AuthenTrend, Aver, Aware, Bank of America, Bastille, Behaviosec, BioCatch, BioConnect, BIO-key, BioTrust, Boku, Bolt, buguroo, Callsign, Cleafy, Daon, DataVisor, Delta ID, Digital.ai, Duo, Early Warning Services, Ekata, Entersekt, Entrust, Equifax, Experian, F5, Facebanx, Facebook, FacePhi, FaceTec, FEITIAN, FICO, ForgeRock, Fourthline, Fraud.net, FraudHunt, GBG, Google, Hanko, HID Global, Hypr, IBM Trusteer, ID Insight, ID R&D, IDEE, Idemia, iDenfy, IDMERIT, IDology, Incognia, Innovatrics, Innovis, Intellicheck, IPQualityScore, iProov, Ipsidy, Iris ID, Jumio, Kasada, Keyless, Kofax, LastPass, LexisNexis Risk Solutions, LoginRadius, MaxMind, Melissa Data, MicroBilt, Microsoft, Mitek, Monapi, Mozilla, Neothone, Neuro-ID, Neustar, NEXT Biometrics, Next Caller, NICE, Nok Nok Labs, Nuance, NuData Security, Okta, OneLogin, OneSpan, Oneytrust, Onfido, Optimal IdM, PayPal, PerimeterX, Pindrop Security, Ping Identity, Pipl, Pradeo, Precognitive, Prove, Radware, Refinitiv, RSA Security, Samsung SDS, Secret Double Octopus, SecuGen, SecureAuth, SecuredTouch, Seon, Shufti Pro, Signal Sciences, Socure, SoloKeys, SpyCloud, StoneLock, StrongKey, SurePassID, Swoop, TECH5, Thales, ThreatMark, TowerData, Transmit Security, TransUnion, Trulioo, Trusona, TrustID, TypingDNA, Uniken, Veratad, Veridas, Verint, Wells Fargo, XTN, Yubico, Zimperium, and Zumigo.
About the Author

David Mattei
David Mattei is a Strategic Advisor at Datos Insights in the Fraud & AML practice. David has over 15 years of experience in the payments industry designing, building, and launching fraud and dispute systems. Fraud constantly poses financial and reputational risks to parties on both sides of a transaction, and David's customers have included merchants and financial institutions, giving him...
Other Authors
Datos Insights
We are the advisor of choice to the banking, insurance, securities, and retail technology industries–both the financial institutions and the technology providers who serve them. The Datos Insights mission is to help our clients make better technology decisions so they can protect and grow their customers’ assets.
