Boston, September 10, 2019 – Exploiting atype of breach called formjacking, Magecart group hackers inject an e-commerce checkout form with malicious code that sends buyers’ credit card information to an offsite server under the hackers’ control. These groups then sell the credit card numbers on the dark web and use the credit cards to purchase high-cost goods in the United States and resell them in other markets. In-app code obfuscation and tamper detection can alert to and prevent formjacking, but e-commerce web applications that aren’t being properly secured with these in-app protections have created a massive attack surface.
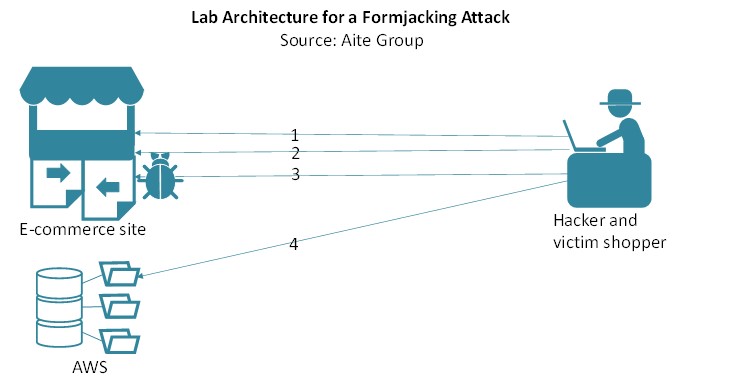
This research, sponsored by Arxan Technologies, follows the trail of servers compromised by Magecart groups as well as the collection servers to which the sites were actively sending stolen credit card data. The data forming the basis of this report was collected and analyzed by Aite Group using primary research methods to discover 80 compromised e-commerce sites globally. The report reveals the vulnerabilities that the group exploited to gain unauthorized access to the sites and to inject formjacking code into the sites’ checkout forms.
This 33-page Impact Report contains 15 figures and one table. Clients of Aite Group’s Cybersecurity service can download this report, the corresponding charts, and the Executive Impact Deck.
This report mentions Adobe, Anomali, Apple, Arxan Technologies, British Airways, eMarketer, Flashpoint, Forbes, Google, Krebs on Security, Malwarebytes, RiskIQ, Symantec, pastebin.com, Shopify, and ZDNet.
About the Author
Datos Insights
We are the advisor of choice to the banking, insurance, securities, and retail technology industries–both the financial institutions and the technology providers who serve them. The Datos Insights mission is to help our clients make better technology decisions so they can protect and grow their customers’ assets.