How Tokenization and Encryption Can Take the Wind Out of a Hacker's Sails
Report Summary
How Tokenization and Encryption Can Take the Wind Out of a Hacker's Sails
Devaluing sensitive data is the best offense in the cyberwar—tokenization and encryption are key tools.
Boston, October 1, 2014 – Security breach. Data compromise. Hacked. These words keep chief information security officers awake at night, and it's no wonder that security professionals, vendors, and global standards committees are actively working to defend against cybercriminals' increasingly sophisticated attacks. But can their innovative encryption and tokenization technologies not only slacken the pace of these attacks but also leave the hackers dead in the water?
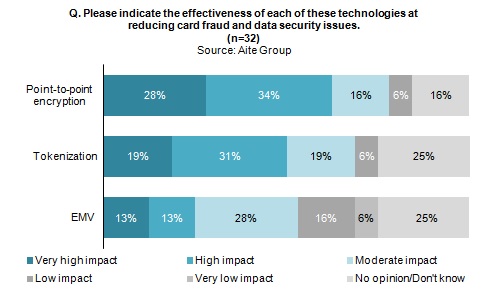
This Aite Group Impact Note is based on 2014 interviews with financial technology executives and product managers and will examine recent security breaches, the point of compromise within the most prominent 2013 breach, and the technologies available to protect organizations from exposing valuable customer information.
This 22-page Impact Note contains eight figures and three tables. Clients of Aite Group's Fraud & AML service can download this report.
