As the economy transitions from post-COVID to prerecession conditions, a sea of change is washing over the cybersecurity industry. Changing economic conditions and evolving approaches to secure digital assets will create a frothy cybersecurity sea in 2023 for chief information security officers (CISOs) and other risk leaders at financial services firms.
These changes will be good for some and not so good for others. The not-so-good has come to technology vendors selling to financial services firms who have been forced to make tough choices, including laying off personnel. In contrast, the good has come to the private equity community, which has taken advantage of depressed company values to build up investment portfolios.
The business of protecting information and assets must continue. Cybercriminals are becoming more advanced—hiding behind deepfake personas and targeting a gateway vector to the attack surface: application programming interfaces (APIs).
Once-promised secure approaches to protecting information and assets, such as blockchain and multi-factor authentication (MFA), have fallen victim to adversaries to the point where the government has weighed in with regulations and oversight. Financial institutions (FIs) are looking for force multipliers and have started to converge the domains of cybersecurity and fraud to get a leg up on attackers.
Aite-Novarica Group has identified 10 trends that will shape the cybersecurity industry in 2023 and beyond for banks and financial services firms.
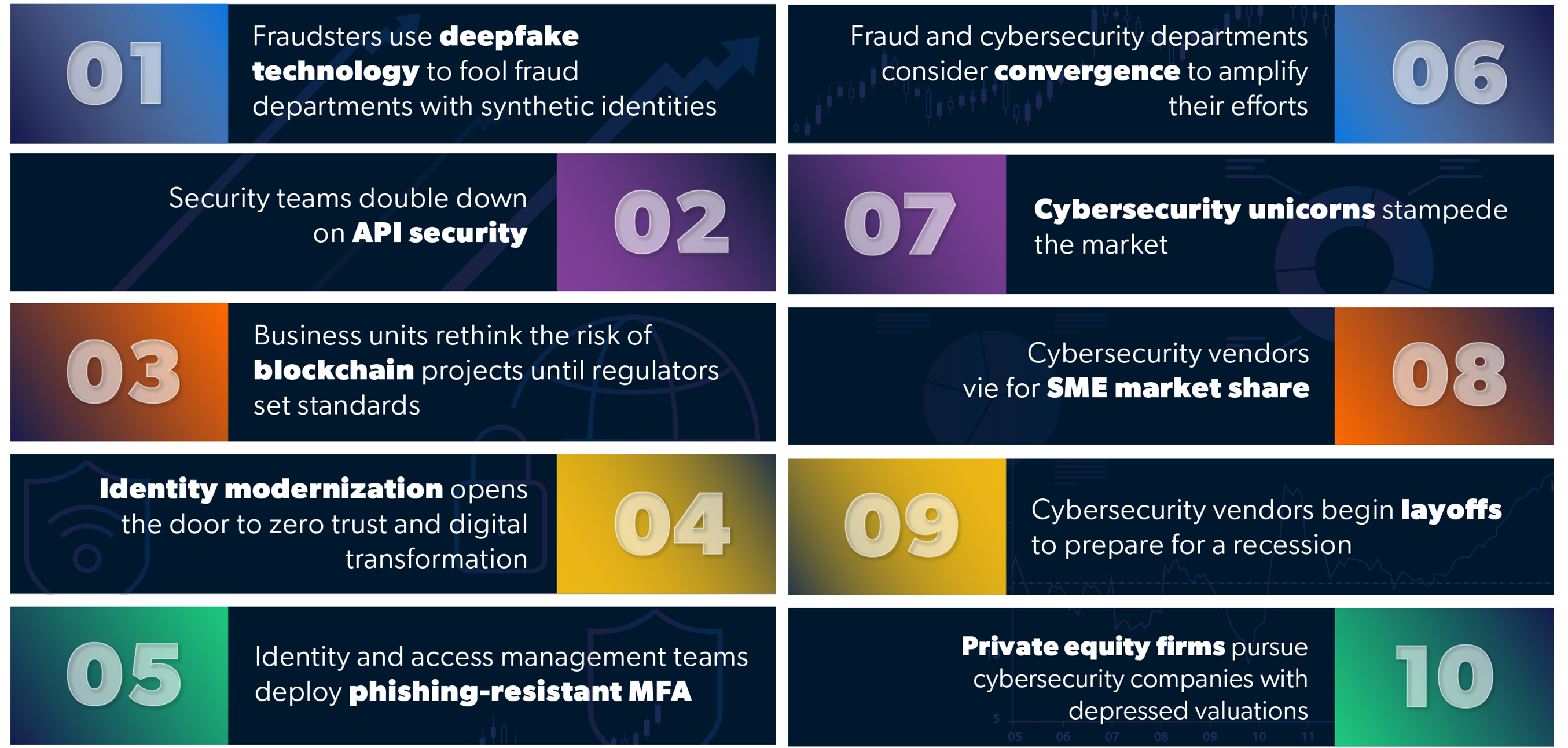
Here are three trends that CISOs will be talking about first:
- Security teams double down on API security.
Aite-Novarica Group believes that API security vulnerabilities will increase substantially in 2023. Salt Labs, an API protection solution provider, reported in its 2022 State of API Security report that 95% of organizations running production APIs had experienced an API security incident. Since 1999, there have been nearly 3,500 vulnerabilities related to APIs.
Sutton’s Law was born when the famous bank robber Willie Sutton was asked why he robbed banks, and he responded, “because that’s where the money is.” Sutton’s Law states that you should first pick the most likely cause and test for that. If one were to ask a hacker why they attack APIs, it’s because it is the gateway to applications and services. If you gain access to APIs, you have the keys to the kingdom.
Although protecting APIs should be fundamental to any cybersecurity strategy, it is often overlooked or poorly implemented.
The four principal APIs—public, private, partner, and composite—carry risks. Financial services firms and banks may protect one or two types well, but they rarely protect all four API types. The need for API security is anything but new; Salesforce and eBay began exposing APIs to interact with their apps over 20 years ago, and the CVE database reported its first API vulnerability in 1999.
The digital economy has driven API growth; now, over 200 million public and private APIs exist. This number of APIs represents a huge attack surface that will increasingly garner the attention of hackers. The growing threat to APIs has spawned a market of API security products offered by Cequence Security, F5, Noname Security, Salt Security, Radware, and others. Look for Aite-Novarica Group’s API landscape and Matrix report in early 2023.
- Fraud and cybersecurity departments consider convergence to amplify their efforts.
The convergence of fraud, AML, and cybersecurity has been the topic of considerable attention during the past 15 years. Conceptually, this makes perfect sense: These risk functions represent an intertwined continuum, with commonality among attacks, bad actors, and outcomes. However, the reality of enabling greater convergence among these silos has proven much more easily said than done for many financial services firms, particularly larger ones.
In terms of convergence, neobanks, fintech lenders, payment firms, and smaller FIs have led the way. Fintech startups often operate from a more integrated perspective since they aren’t burdened by legacy technology and organizational silos. Smaller FIs often take the convergence approach through sheer necessity since their resource pool is much smaller than that of their larger brethren. Large FIs have been slow followers, but the industry is now seeing acceleration as several early adopters of the “fusion center” concept are starting to reap tangible benefits.
The obstacles for larger firms are not insignificant. Cybersecurity, fraud, and AML in larger FIs have typically been siloed functions with discrete and often very different performance objectives. Human nature rears its head in discussions about organizational convergence, with people concerned over the stability of their job and career path. And there is a great deal of inertia associated with the legacy technology implementations—rip-and-replace efforts to enable technology that can better facilitate greater convergence and collaboration are often quite challenging from an IT resource and budget perspective.
As more firms progress toward greater collaboration and convergence among their risk functions, Aite-Novarica Group expects to see this have a snowball effect as best practices are disseminated. Over time, financial crime convergence will also become a competitive imperative, as those that excel on this front will be better prepared to defend against criminal activity than their peers.
- Identity and access management teams deploy phishing-resistant MFA.
MFA solutions for users have existed for two decades. They allow businesses to be more confident that users are actually who they say they are. Pandemic dynamics revealed that many well-known “traditional” MFA solutions are no longer fit for purpose. Attackers have been able to beat even strong passwords, knowledge-based authentication, and one-time passcodes sent through standard SMS messaging.
Phishing of a password or personal identification number is often the root cause of a breach. In August 2022, the so-named Oktapus attack campaign was reported by cybersecurity provider Group-IB. Attackers breached Twilio and Cloudflare using text message phishing, ultimately compromising nearly 10,000 Okta credentials spanning 136 organizations.
This successful attack served as the poster child for 2022 and illustrated that workforce employees can be just as vulnerable as consumers to phishing attacks. Traditional MFA methods no longer provide the security assurance they did two decades ago; they are no longer fit for current business purposes for banks and other financial service institutions.
Risks associated with traditional MFA are not new; seasoned CISOs and information security professionals have understood them for years. CISOs at many banks and financial services firms are expected to prioritize deploying phishing-resistant MFA in 2023, driven by cyber and reputational risks and the increased regularity of successful attacks beating traditional MFA.
Deployments this year may be limited to areas of the business exposed to the highest risk, addressing other areas of the business in 2024. Aite-Novarica Group believes that federal or state regulatory authorities will likely mandate phishing-resistant MFA deployments sometime in 2023, driving compliance-driven efforts.
To view the complete list of Aite-Novarica Group’s Top 10 2023 trends for the cybersecurity industry, read our report Top 10 Trends in Cybersecurity, 2023: A Sea of Change for the Industry. You can also watch the recording of our February 8th webinar, where we explored each of these trends in detail. Click here to access the recording.