With the rise of the hybrid, work-from-home workforce and increasing global distribution of corporate information and network assets, financial services (FS) and banking organizations are rethinking how they can effectively protect data. FS chief information security officers (CISOs) are prioritizing implementation of zero-trust architecture (ZTA) because the traditional information security approach—characterized as “defending the perimeter”—is inadequate to guard against the risk of cyber threats to the organization’s IT assets and data.
ZTA changes the paradigm of information security strategy; its central tenet is that no one, including any employee or partner already inside the IT network, can be trusted. FS CISOs should assume that malicious attackers are no longer trying to enter at the gates, or boundaries, of the corporate network—cyberattacks now bypass perimeter protections (e.g., firewalls) through compromising identities and access points (e.g., phishing emails and encrypted malicious code injections).
In this blog, I will explain the imperative to adopt ZTA as principal design scheme that is part of the organization’s overall information security architecture and share guidance on how FS CISOs should think about a comprehensive approach to integrating ZTA.
Zero-Trust Architecture Is Essential
Given the reality of distributed workforces and data, the FS and banking industries require a security architecture model that establishes comprehensive, enterprise-wide data and information protection. ANG’s review of the latest Federal Financial Institutions Examination Council (FFIEC) guidance suggests that FS CISOs should prioritize integration of ZTA design within their organization’s overall information security program.
Data and information are no longer confined behind corporate firewalls as employees, devices, customers, and partners are dispersed in terms of both where and how they access the corporate network and applications. Therefore, security strategy should be oriented around both data protection at the network perimeter and laterally within the enterprise encompassing physical, online, and cloud environments.
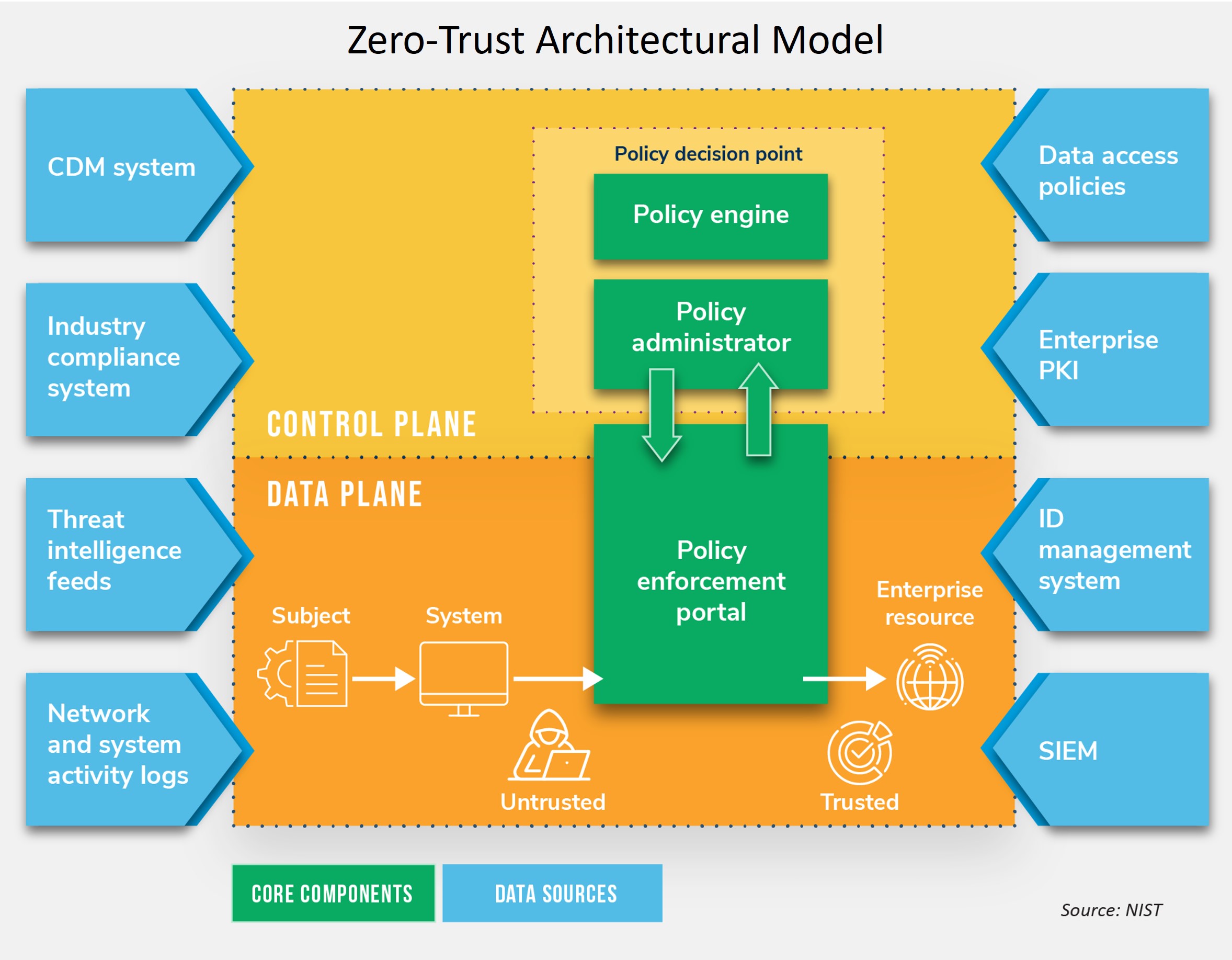
The ZTA model is intended to build an information security architecture that effectively protects dispersed networks of data and applications because of its core architecture design principles.
Threats Are Inside the Perimeter
ZTA is based on the fundamental principle that malicious attackers (i.e., threats) are already in the organization’s IT network and because aggressors have breached the network, the ZTA model does not automatically trust users granting them access to data and applications. Therefore, threats that have fallen through perimeter security defenses can be contained.
FS CISOs should leverage this principle as a starting point to address the logical design components that protect data from bad actors moving laterally across information assets within the network. It is essential to address these design components, such as the policy engine and ID management system, to fully implement a ZTA security architecture that prevents threats moving inside the IT network.
To help CISOs prioritize the components of a comprehensive approach to zero-trust deployments, ANG created a ZTA conceptual model and curated a design checklist. These tools are included in ANG’s new brief CISO Guidance for Zero-Trust Architecture and facilitate conducting a quick and thorough assessment of how effectively an organization’s overall information security program incorporates ZTA.
Readiness Assessment Should be Performed
As discussed in the brief, ANG recommends that CISOs conduct a ZTA readiness assessment covering both the design and the technology-related components (providers and practices) required for effective implementation. The readiness assessment is similar to conducting a heat map exercise and essential to verifying adherence to a standardized model.
CISO Guidance for Zero-Trust Architecture provides an actionable roadmap to conduct this readiness assessment and guide implementation of a comprehensive ZTA approach, avoiding an incomplete deployment that leaves FS organizations vulnerable to cyberattacks. To assist CISOs with effective implementation, ANG mapped the logical design components to a standardized, trustworthy framework outlined in the NIST Special Publication 800-207 and Cyber Security Framework (CSF).
First, it is essential to identify where gaps exist in completing the integration of ZTA design across policies, procedures, processes, practices, and technology solutions. Second, the assessment should be performed “to understand the existing solutions that may be used to address the technical enforcement aspects of zero trust.” As the market for technology providers offering ZTA solutions proliferates, FS CISOs should undertake a mapping of potential technology solutions to the main design components in making the appropriate selections.
As stated in our new brief, “Zero trust is here to stay; CISOs should prioritize this but ensure proper design and architecture are applied to avoid piecemeal adoption.” By starting with the fundamental principle that cyber threats are already inside the IT network, FS and banking institutions should implement ZTA to establish an end-to-end security architecture that curtails attackers by preventing malicious east-west movement across information assets.
An Invitation for You
Are you an FS/banking CISO or senior security executive? Would you like more information about joining our exclusive Financial Services CIO/CTO Advisory Research Council? We’d love to hear your guidance on how this new offering can support your function’s impact.
Simply click the link below to share your contact information, and I’ll reach out to schedule an introductory conversation about the new Financial Services CIO/CTO Advisory practice and associated Research Council. You’ll also receive a free copy of our brief CISO Guidance for Zero-Trust Architecture.
Add new comment