With workforces and organizational data assets scattered globally and corporate networks being accessed remotely, the financial services (FS) industry is increasingly susceptible to cybersecurity breaches. In this dispersed environment, attackers target remote workers and unsecure personal devices by compromising identities to circumvent traditional network security policies. These cyberattacks then move laterally inside the network to seize data and facilitate ransomware and other malware attacks.
Given the heightened risk of a significant security and data breach, it’s unsurprising that a top priority of FS chief information security officers (CISOs) is adopting a zero-trust architecture (ZTA). From its central tenet that no one can be trusted, including any employee or partner already inside the IT network, zero trust is designed to protect data and applications across the enterprise by limiting access privileges.
This post will explore the nature of cyberattacks today and describe how a comprehensive ZTA security approach enables enterprise data protection through real-time, continuous authentication using a combination of tools working together.
Cyberattackers Are Already Inside
FS organizations are more vulnerable than ever to cyberattacks because of distributed networks and remote workforces. Traditional perimeter defenses are inadequate to prevent security breaches or theft of corporate information and customer data as savvy attackers compromise identities to easily bypass firewalls and other cybersecurity protections (e.g., anti-malware software).
For example, phishing emails, distributed denial of service attacks on cloud providers, and malware attacks on endpoints (e.g., remote devices) pose increasing risk to the integrity of FS organizations’ IT networks and data. These cybersecurity threats are more insidious because network perimeter-focused information security programs cannot detect when the identity of a previously verified user or device is subsequently compromised.
Zero Trust Requires Real-Time Authentication
To defend against cyberattacks that compromise identities, FS CISOs should implement a comprehensive security architecture program that focuses on data protection. ZTA is an information security architecture approach that protects data because it is grounded in the fundamental assumption of no trust; users and devices are not automatically granted access to data and applications. All users and devices must be authenticated when a unique access request is made from any network connection, without exception.
As stated in Aite-Novarica Group’s new brief CISO Guidance for Zero-Trust Architecture, “access to individual enterprise resources is granted on a per-session basis.” Consequently, no user/device that is logged on and subsequently compromised carries over previous authentication and authorization to another resource on the network—i.e., access to network applications is granted each time a request is made.
Authentication is also “dynamic and strictly enforced before access privileges are granted,” resulting in an information security posture of continuous identity verification for all identities inside the IT network.
To implement a proper ZTA design that effectively defends against cyberattackers already inside the network, technology solutions are required to address gaps for the majority of FS organizations.
Financial Services ZTA Implementation
As stated in CISO Guidance for Zero-Trust Architecture, “zero trust is not a singular technology but rather an end-to-end architecture composed of policies, procedures, processes, practices, and a technology stack designed to prevent east-west malicious movement.” Therefore, to avoid piecemeal implementation of ZTA as part of the organization’s overall information security program, FS CISOs should select the appropriate technology solutions that collectively address all logical zero-trust design components.
The logical components of an authoritative ZTA approach are outlined in the brief and include the policy engine, the continuous diagnostics and mitigation (CDM) system, and threat intelligence feeds. As there is no single tool or solution that provides complete coverage of all ZTA design components, CISOs need to determine the appropriate mix of technology providers that enable implementation of a comprehensive design.
To help visualize how to select technology solutions and providers, Aite-Novarica Group developed a sample technology capability map that avoids piecemeal implementation. For example, as the graphic shows, FS organizations could select three market-leading providers covering identity and access management (IDAM), threat and vulnerability management (TVM) and governance, risk and compliance (GRC) that in combination fully align to the complete, authoritative ZTA model.
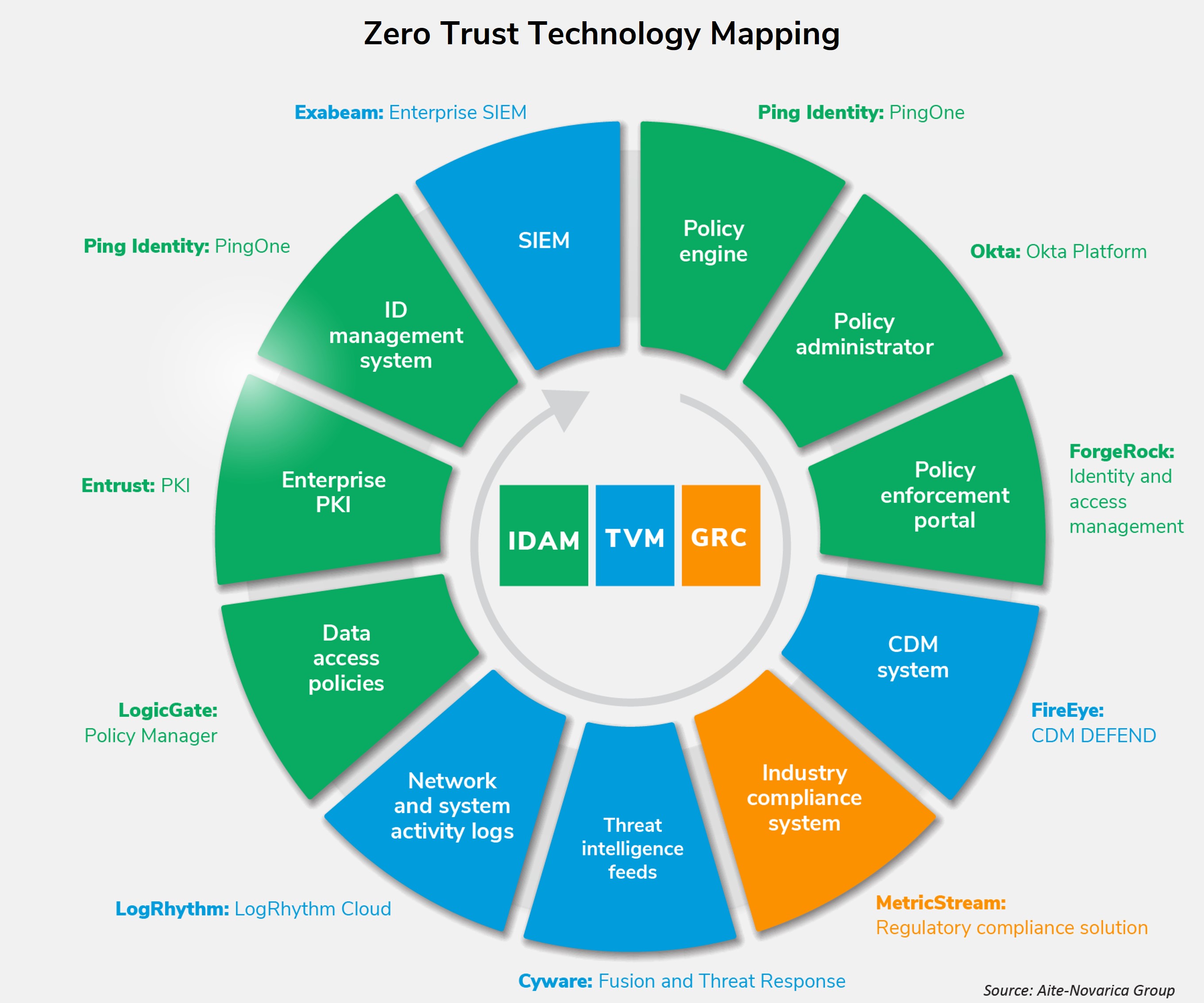
Selecting technology providers starts with design principles and components on which a comprehensive ZTA model implementation is centered and not with the marketing claims of cybersecurity providers.
By assuming that malicious attackers are already inside the organization’s IT network, ZTA enables more comprehensive data protection by preventing users and devices from moving east-west to access other parts of the network until they have been authenticated. FS organizations should implement a comprehensive ZTA security approach by leveraging the appropriate combination of technologies to create an end-to-end security architecture that protects enterprise data from complex cybersecurity threats.
An Invitation for You
Are you an FS/banking CISO or senior security executive? Would you like more information about joining our exclusive Financial Services CIO/CTO Advisory Research Council? We’d love to hear your guidance on how this new offering can support your function’s impact.
Simply click the link below to share your contact information, and I’ll reach out to schedule an introductory conversation about the new Financial Services CIO/CTO Advisory practice and associated Research Council. You’ll also receive a free copy of our brief CISO Guidance for Zero-Trust Architecture.
Add new comment